You’ve set up your wallet, linked your card, and granted permissions. Then comes the call or SMS: “There’s a problem with your account.” A few taps later, your money is gone.
In Southeast Asia’s super app landscape, seamlessness can be a double-edged sword; what feels frictionless for users can also lower the barrier for bad actors. As platforms expand services and link more accounts, trust becomes more than branding; it’s architecture, transparency, and user control.
In Part 2, we explore how platforms like Touch ’n Go, Grab, and GoTo handle that responsibility. While features like refund guarantees, safety toggles, and fraud detection hubs exist, the real test is how they perform under pressure—and what platforms don't always say out loud.
1. Touch ’n Go eWallet: Promises and Loopholes
The Trust Pitch and the Hidden Gap
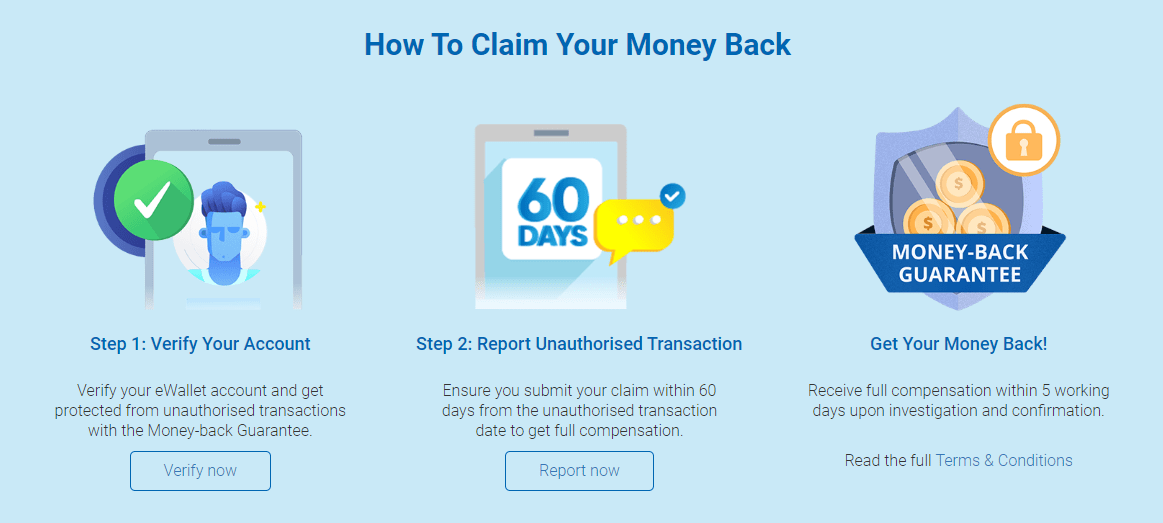
Touch ’n Go eWallet presents itself as one of Malaysia’s safest platforms. It offers biometric login, real-time transaction alerts, and a Money-Back Guarantee. These features, on paper, create the impression of full protection.
Yet scams continue to plague users—especially social engineering scams where fraudsters impersonate TNG agents via phone or WhatsApp. In multiple cases, users were tricked into giving OTPs or clicking malicious links.
Despite the “guarantee,” TNG's policy only covers unauthorized transactions reported within 60 days—not scams where users were deceived into authorizing a payment themselves. As user complaints and media reports confirm, TNG often rejects refunds in these scenarios.
What TNG Did: Strengthened Warnings
TNG now prominently displays scam alerts in-app and warns that it never contacts users via personal phone numbers. Its website lists current scam types and urges users not to share OTPs. But technical safeguards remain limited—TNG still relies heavily on users recognizing the scam before acting.

The Outcome
Trust in TNG depends on user vigilance. The super app feels safe, but behind the scenes, the protection system has strict fine print. For users, the takeaway is clear: don’t assume a guarantee means automatic refunds—and don’t trust unsolicited calls, no matter how “official” they sound.
2. Grab: Transparency Wins, But Risks Remain
Clearer Payments, Safer Rides but Limited Transparency
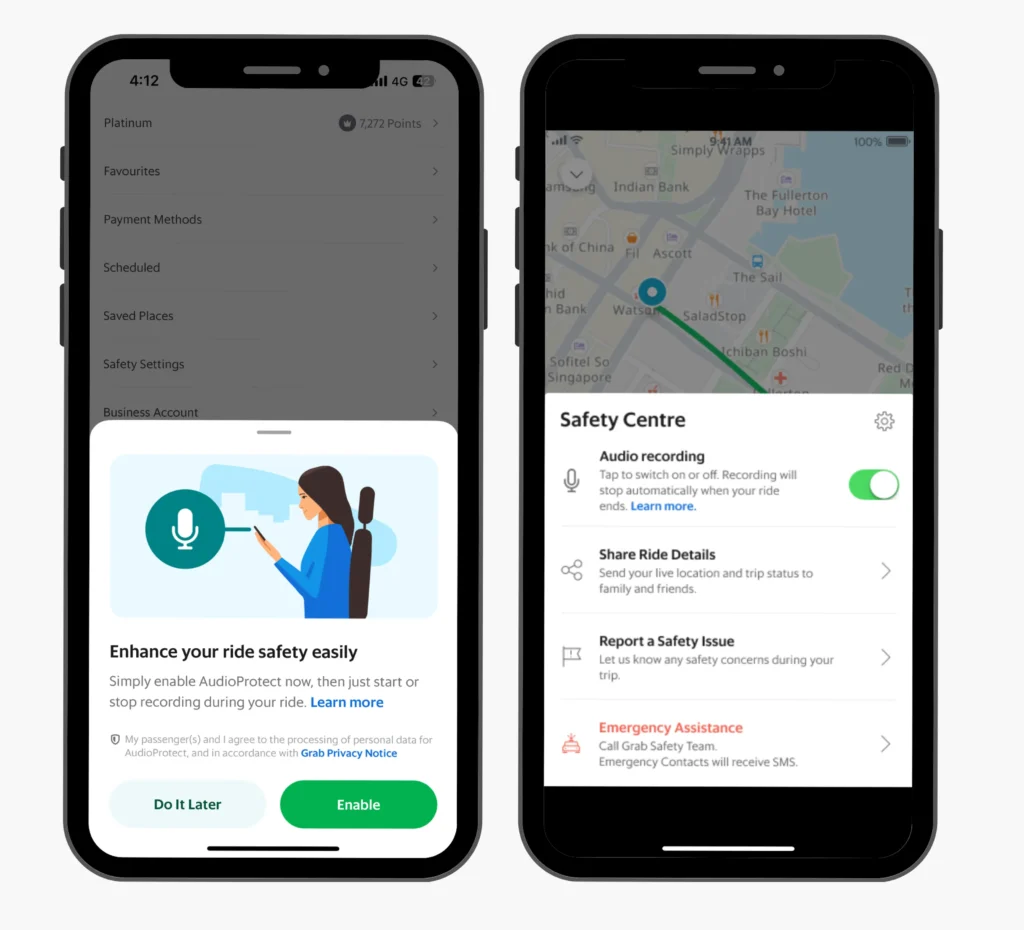
Grab has taken visible steps to build user trust. It introduced up-front billing for rides, contextual notifications for offers, and opt-in safety tools like Quiet Ride and AudioProtect (which records rides for dispute resolution). It also limits popups during payment to reduce friction at sensitive moments.
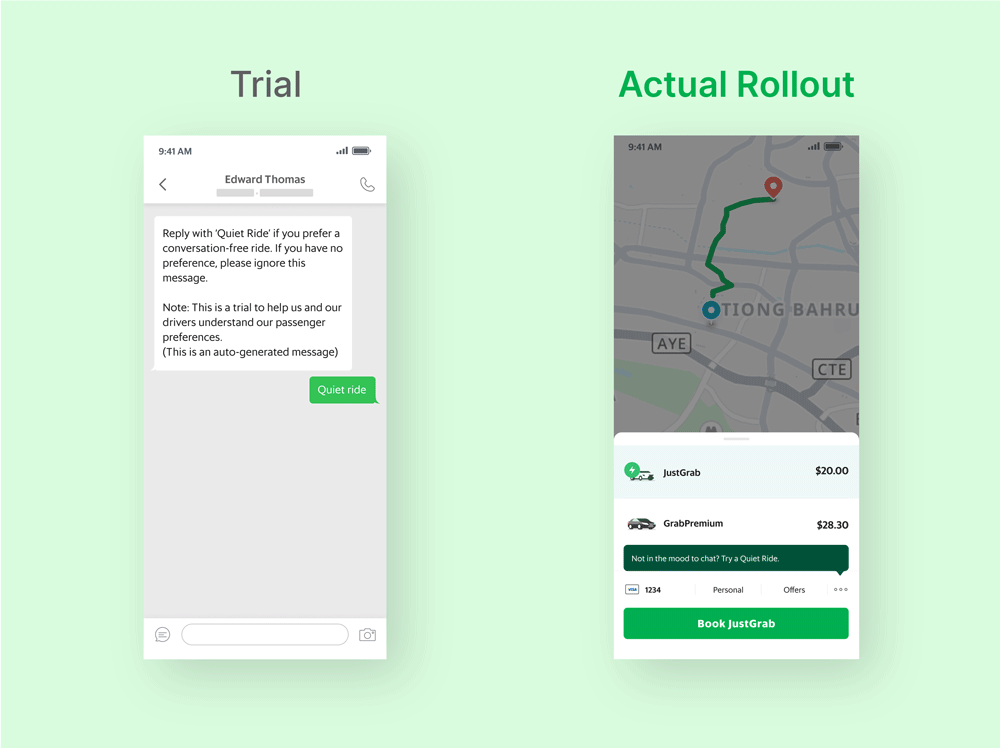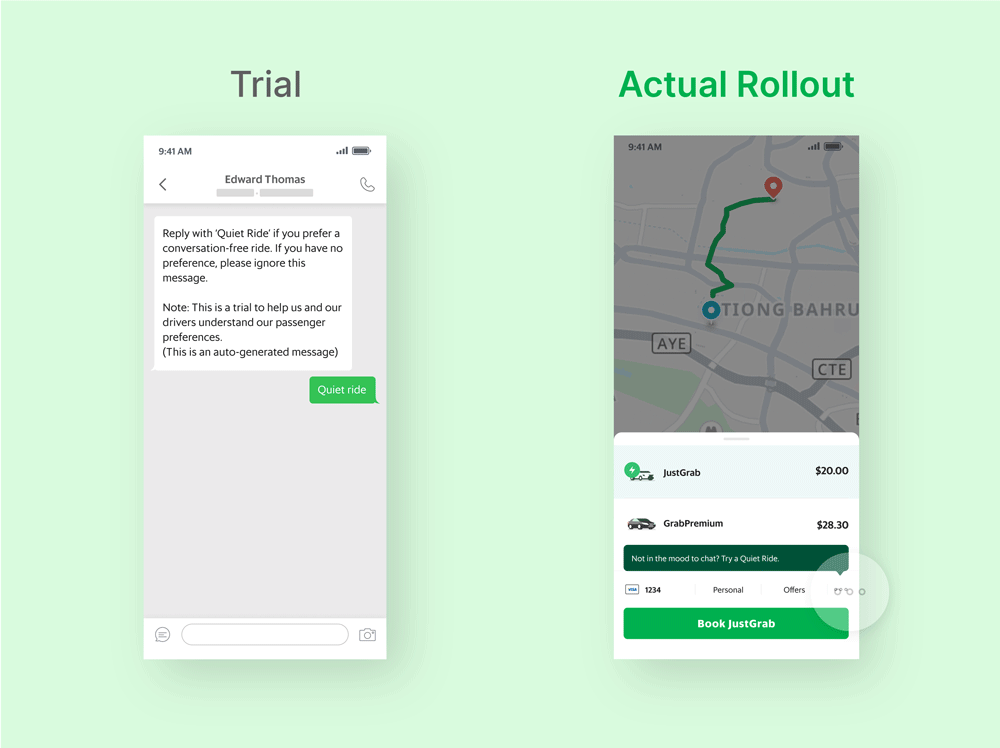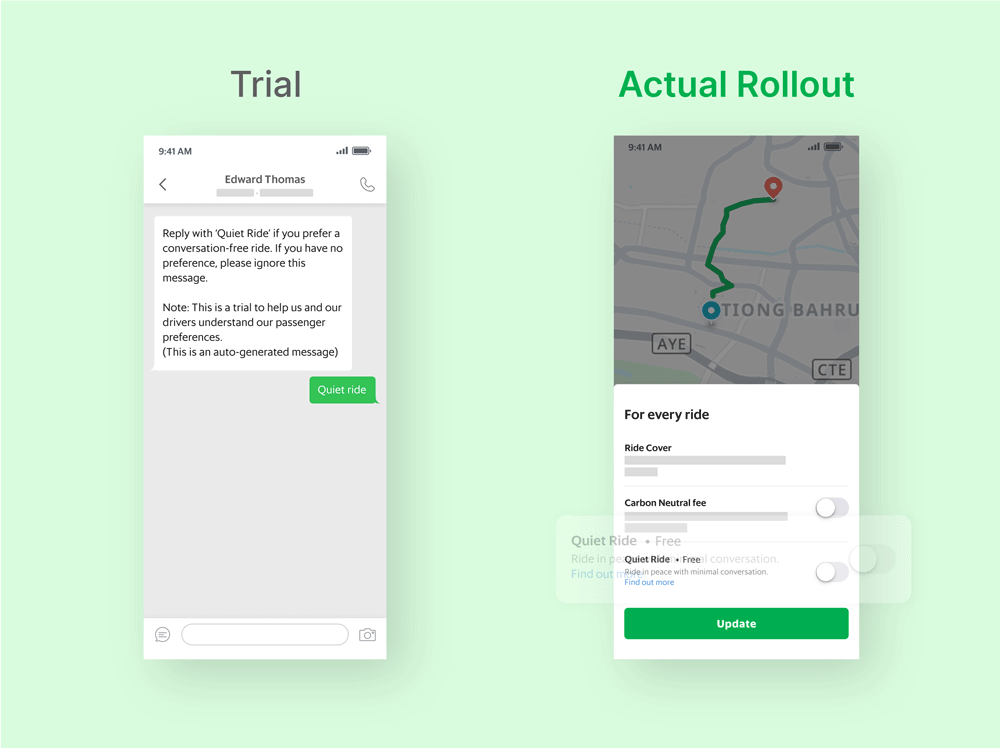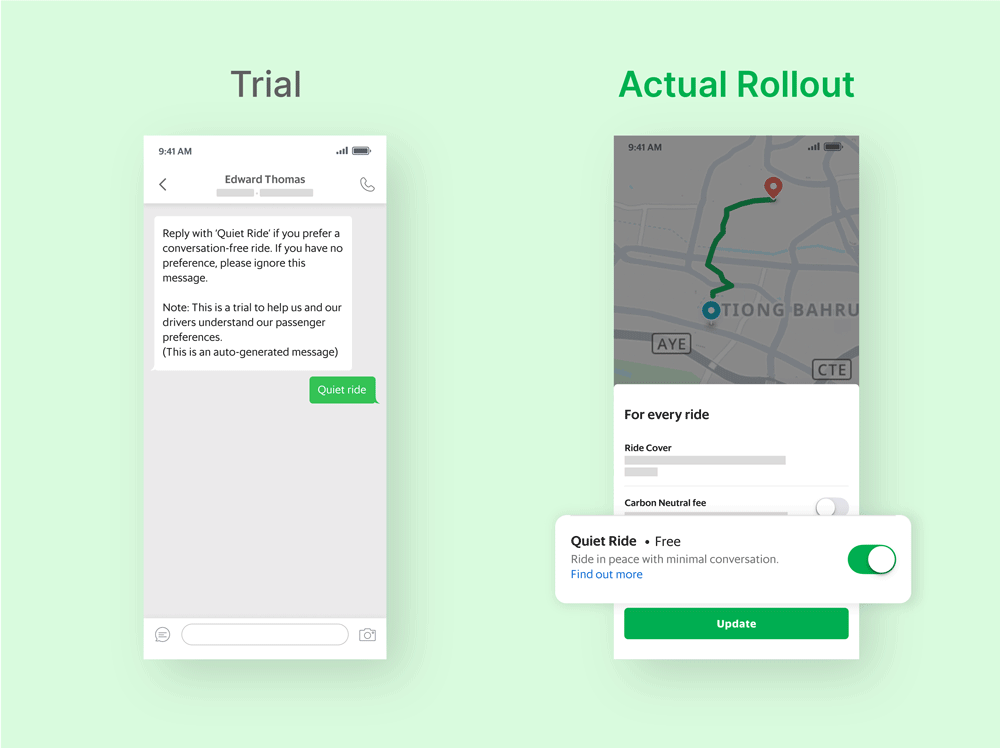
However, despite the transparency in their UX, Grab has faced real privacy and security issues:
- In 2020, the Singapore regulator fined Grab SGD 10,000 after a software update exposed personal data from over 21,000 users—names, trip histories, and more.
- GrabPay lets users skip OTPs for certain linked-card transactions after device activation—creating risk if a phone is stolen or malware-infected.
What Grab Did: More User Control
To address concerns, Grab expanded controls in its privacy dashboard and implemented biometric verification for sensitive actions. Its safety features are now opt-in (like ride audio recordings), and customer education around scams is more prominent in-app and via emails.
The Outcome
Grab’s approach earns points for visibility and UX clarity, especially with opt-in safety features like Quiet Ride and AudioProtect that give riders more control over their comfort and security.
But these tools work best alongside informed digital habits; users must still take steps to secure their devices and understand how Grab handles stored payment data. The best experience still requires informed consent, not blind trust.
3. GoTo: Integration Comes With Oversight
The Scale Challenge
GoTo is the product of two giants—Gojek and Tokopedia—merging ride-hailing, shopping, payments, and more. Their strategy of “split but linked” apps (shared wallet, loyalty, UI components) keeps UX manageable. But the trust dimension is harder.
Tokopedia’s 2020 breach saw hackers claim personal details from 91 million users—a serious warning about centralizing sensitive data. Though passwords were reportedly hashed, names, emails, and birthdates were leaked and offered for sale on the dark web.
What GoTo Did: Improved Privacy Governance
GoTo updated its privacy policy post-merger and now includes consent withdrawal mechanisms. It also committed to build “world-class security technology” under a dedicated data-protection office. But questions remain:
- The Indonesian competition watchdog has reviewed the merger for monopoly concerns.
- In 2025, GoTo’s Jakarta office was raided in a corruption probe related to a third-party government contract—raising questions about broader governance.
The Outcome
GoTo’s UX feels connected but clean. However, trust is still catching up to the product experience. As integrations deepen and more data flows through its platform, the company will need to proactively address past security lapses—and maintain strong oversight amid regulatory pressure.
Core Lesson: Trust is Architecture, Policy, and Perception
Security isn’t just about adding a biometric or refund policy—it’s about aligning those tools with user behavior, platform architecture, and real-world attack patterns. When protection fails silently or is misunderstood, users lose more than money—they lose confidence.
Protect: Default to Skepticism
- What it means: Don’t rely on UI alone. Question OTPs, refund claims, or calls—even if they “look” official.
- For users: Less risk of falling for social engineering.
- For teams: Fewer false expectations reduce disputes and improve trust outcomes.
Disclose: Surface the Limits
- What it means: Show users when coverage ends—e.g. if a refund won't apply or what happens in a breach.
- For users: Informed decisions, fewer surprises.
- For teams: Reduced complaints and more targeted feature fixes.
Harden: Build Beyond the UI
- What it means: Protect against edge-case fraud—like token theft, screen overlay malware, or linked-card attacks.
- For users: Protection when judgment fails.
- For teams: Less reputational fallout after incidents.
Super app trust is built not on claims—but on clarity, consistency, and closure when things go wrong. To deliver it, platforms must treat trust not as a feature, but as a continuous system—supported by code, policy, and user understanding.
Interested in how these super apps maintain consistency and avoid becoming clunky monoliths?
Read Part 1 of our Super App series: Super Apps, Super UX? Part 1: Lessons in Modular App Architecture from SEA Powerhouse to see how modular app architecture makes it possible.





